Receive Information
Bring data from multiple sources into one structured system designed for investigations and intelligence, making it easier to spot threats early and act with confidence.
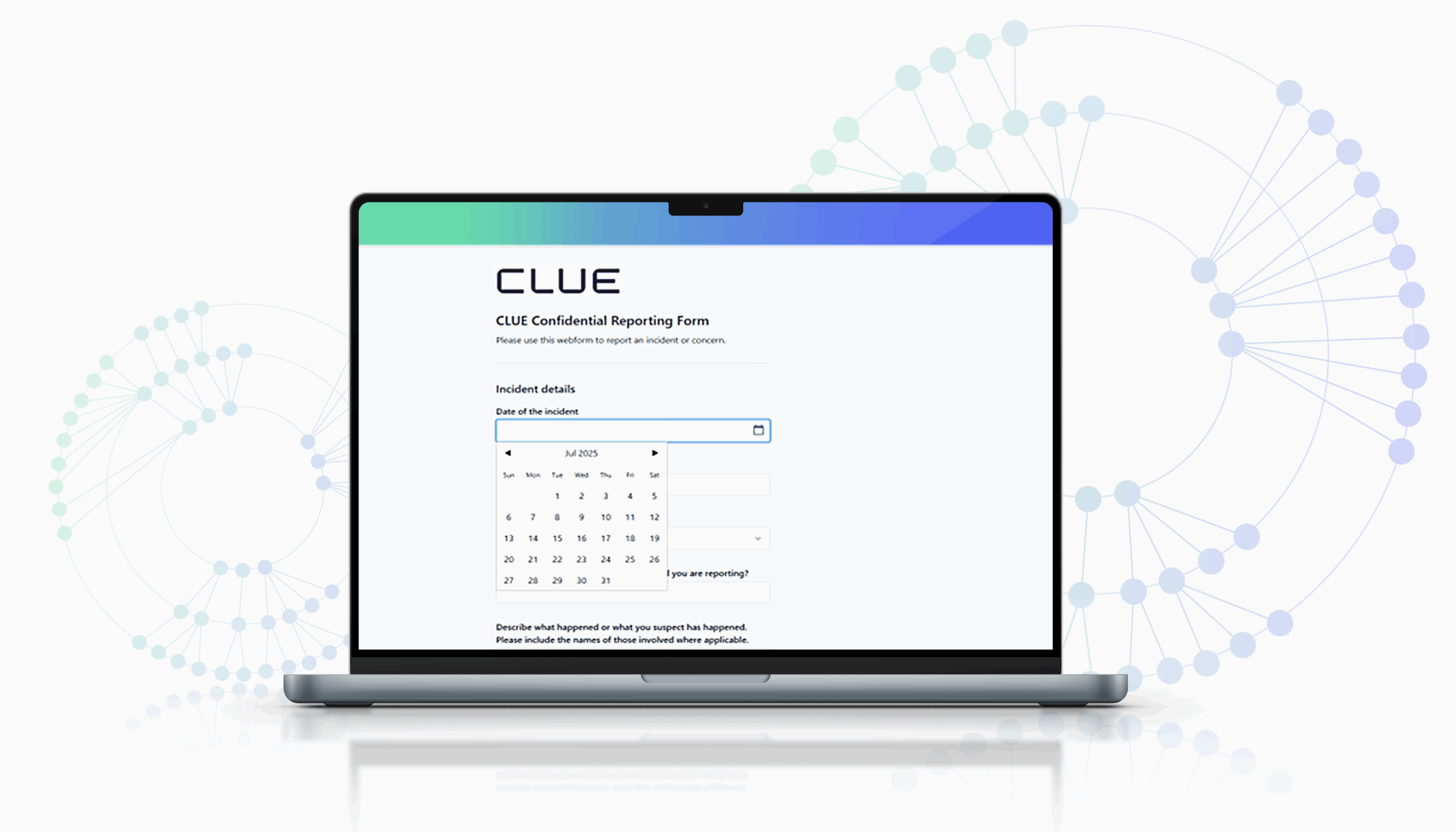
Seamless data capture
Collect information manually or automatically through APIs, webforms, email, or integrations, with multilingual input and a whistleblower option for secure, anonymous reports.
AI-assisted triage (Winter 2025)
Surface key people, organisations, and events with AI-assisted triage, helping to prioritise data and cut through noise while ensuring human oversight, transparency and control.
Proactive monitoring with watchlists
Watchlists use AI to help track the people, organisations, or keywords most relevant to your operations. As soon as new records or patterns match your criteria, Clue notifies you automatically, ensuring priority intelligence surfaces instantly rather than getting lost in the noise.
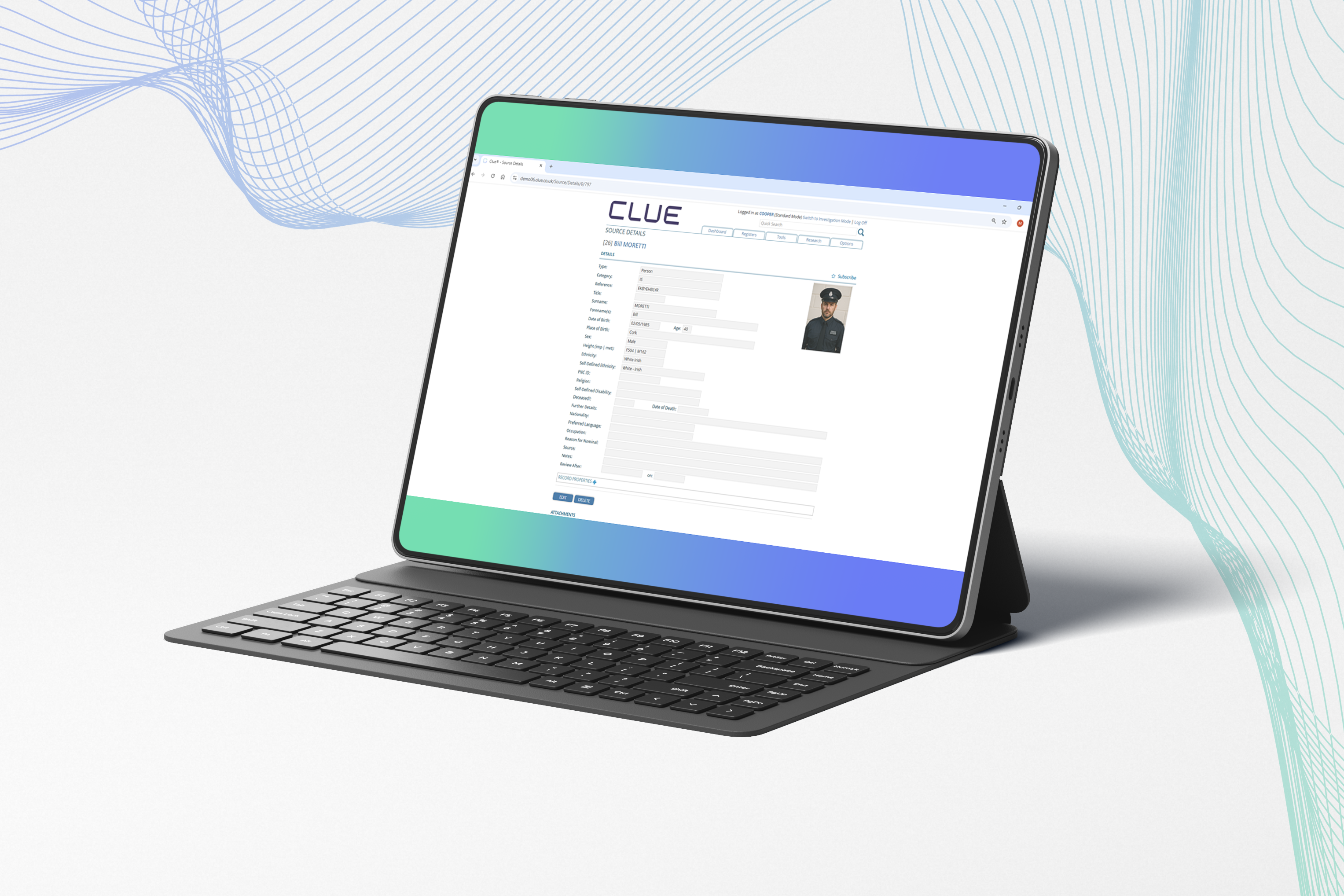
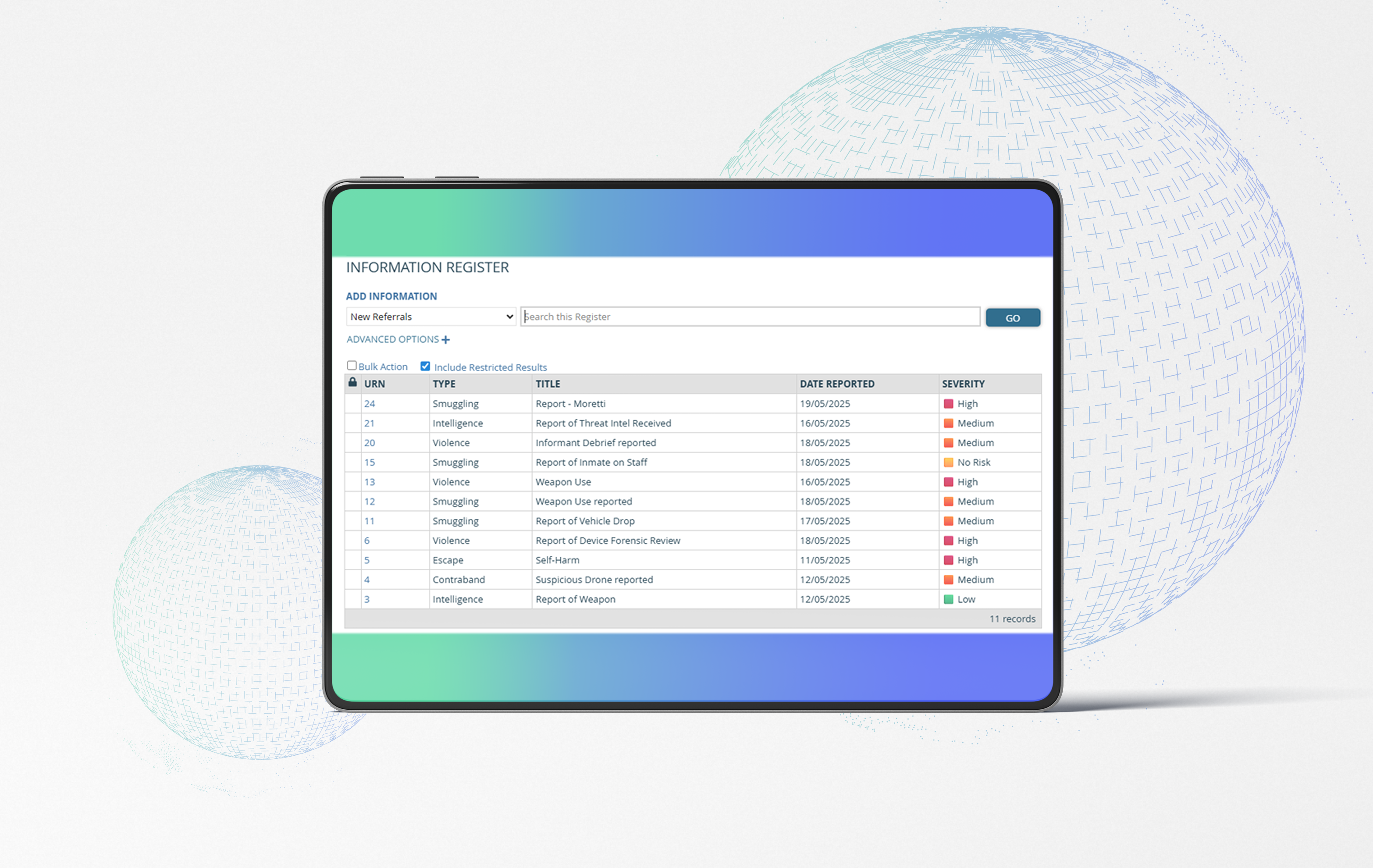
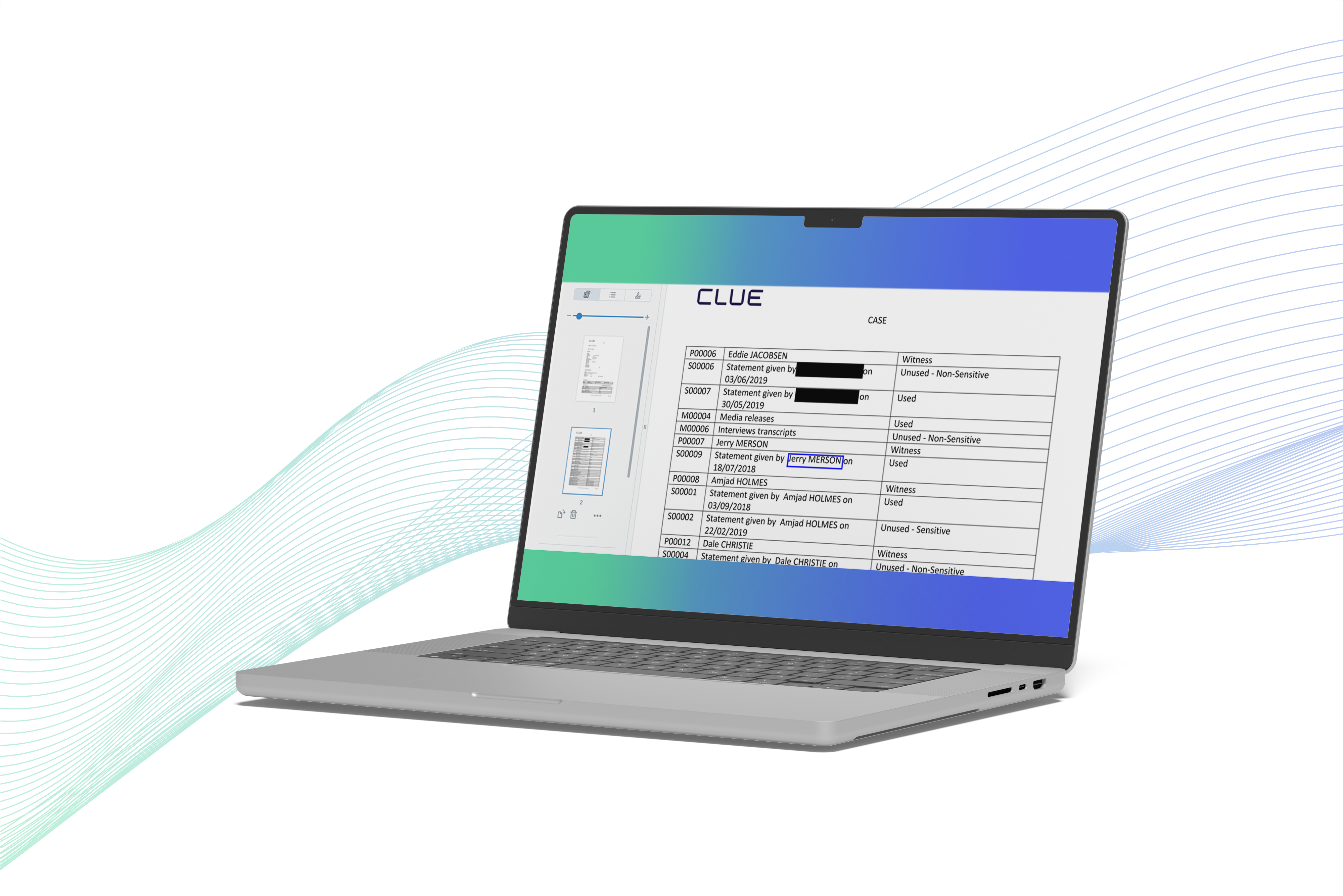
Registers & linking
Log every piece of information in the Information Register, protect contributor identities in the Source Register, and keep people, organisations, and places linked across the system without duplication.
Security, access & compliance
Control access to records, teams, and registers with permissions, protect sources with redaction tools and classification levels, and stay compliant with a GDPR-ready audit trail from day one.
Ready to speak to our experts?
Complete the form and we’ll be in touch to arrange a tailored consultation.
Learn more about Clue
Keep browsing to understand how Clue will help at each step of your operation
- Data unification Consolidate information from every source into one secure system.
- Intelligence development Drive investigations forward with structure and transparency.
- Investigation management Drive investigations forward with structure and transparency.
- Case presentation Package findings, disclose securely, and share with confidence.
- Insight & impact Analyse outcomes to improve performance and prevent harm.
- Trust & compliance Operate securely, ethically, and in line with governance standards.

What's behind the rising insider risk and why does traditional security no longer suffice? Our latest Threat Assessment outlines an intelligence-led approach to detection and prevention, from national security breaches to ransomware.